
Phishing attacks are abusing Microsoft Azure’s Static Web Apps services to steal Microsoft, Office environment 365, Outlook, and OneDrive qualifications.
Azure Static Website Applications is a Microsoft company that assists develop and deploy whole-stack world-wide-web apps to Azure from GitHub or Azure DevOps code repositories.
It makes it possible for developers to use custom domains for branding internet apps, and it delivers world wide web internet hosting for static content material this kind of as HTML, CSS, JavaScript, and visuals.
As protection researcher MalwareHunterTeam learned, threat actors have also seen that the personalized branding and the world wide web internet hosting characteristics can simply be utilised to host static landing phishing web pages.
Attackers are now actively working with Microsoft’s provider in opposition to its prospects, actively targeting consumers with Microsoft, Business 365, Outlook, and OneDrive accounts.
As proven underneath, some of the landing web pages and login kinds used in these phishing strategies appear nearly exactly like official Microsoft pages.
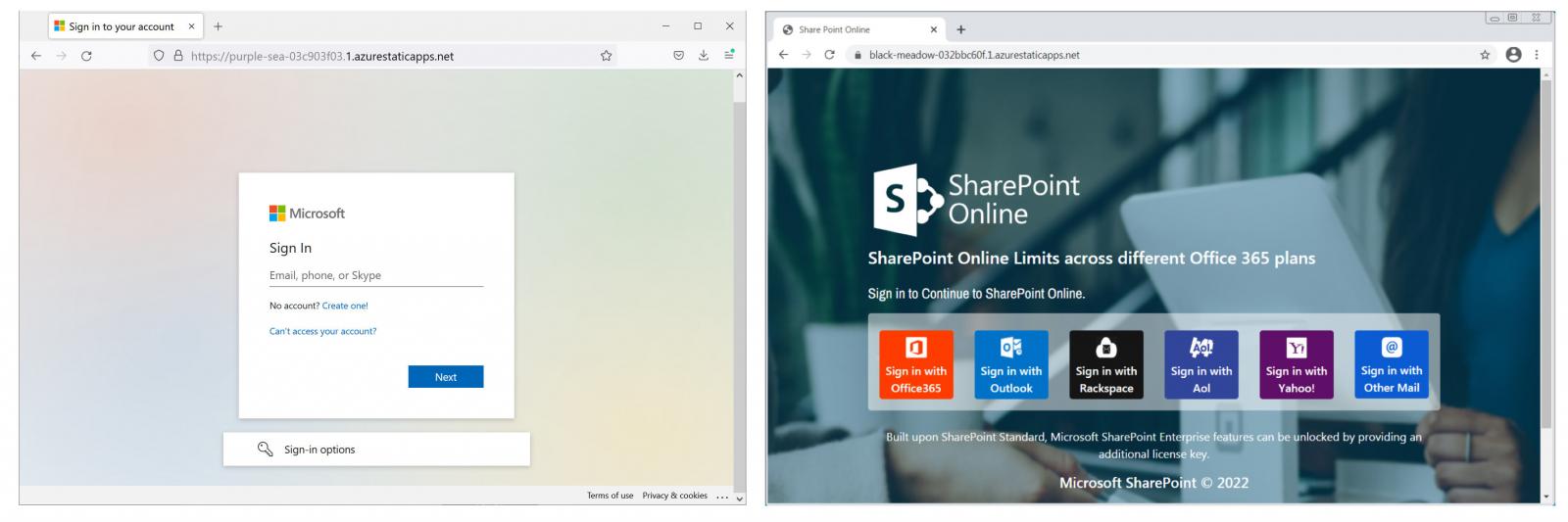
Azure Static Net Apps adds legitimacy
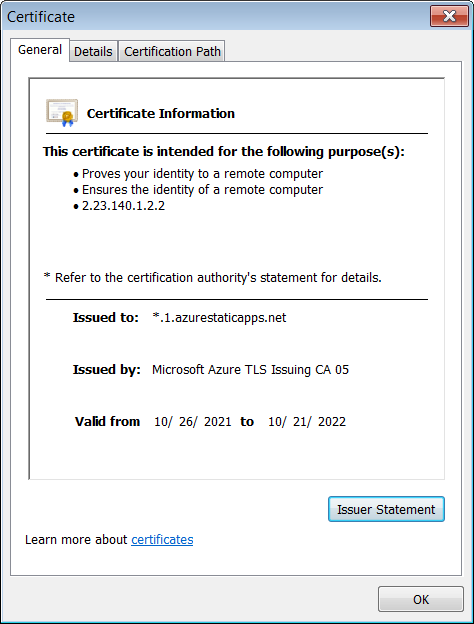
Applying the Azure Static Website Applications platform to concentrate on Microsoft end users is an superb tactic. Every landing website page quickly will get its possess protected site padlock in the deal with bar because of to the *.1.azurestaticapps.net wildcard TLS certificate.
This will likely trick even the most suspicious targets just after seeing the certification issued by Microsoft Azure TLS Issuing CA 05 to *.1.azurestaticapps.net, as a result validating the phishing webpage as an official Microsoft login variety in the eyes of probable victims.
This also will make these landing pages a practical tool when focusing on the buyers of other platforms, together with Rackspace, AOL, Yahoo, and other e mail companies, due to the phony veil of security included by the legit Microsoft TLS certs.
When striving to detect when a phishing attack is concentrating on you, the standard advice is to closely look at the URL when questioned to fill in your account credentials in a login type.
Regretably, the phishing strategies abusing Azure Static Internet Applications make this tips just about worthless since many end users will get tricked by the azurestaticapps.web subdomain and the legitimate TLS certificate.
This is not the very first time a Microsoft assistance has been exploited in phishing assaults to target the company’s personal clients.
Phishing strategies also use the *.blob.main.home windows.net wildcard certificate supplied by Microsoft’s Azure Blob Storage to focus on Office environment 365 and Outlook buyers.
BleepingComputer arrived at out to Microsoft for comment and we’ll update the tale if we listen to back again.
